Using the Data Perimeter to Secure Your Cloud
The InstaSecure Data Perimeter allows you to ensure only trusted parties have access to what they need and prevent all other access.
60%
of Cloud IAM breaches involve credential issues
Misconfigurations and vulnerable software only account for a combined 21% of breaches.
*Based on Q1 2023 observations by Google Cloud IR teams
What Doesn’t Work Against Credential Theft and Zero-Day Attacks?
Trying to perfect Least Privilege policy.
Least Privilege and Zero Trust Microsegmentation only narrows the scope of access and reduces blast radius without addressing the portability issue.
Endless detection and remediation.
These one-off fixes to misconfigurations and known vulnerabilities are labor-intensive, reactive, and never-ending.
Just in Time Access and short-term credentials.
This type of access covers less than 5% of attack surface and has longer authorization than needed. Attackers discover and abuse these short term credentials.
What Does Work Against Credential Theft and Zero-Day Attacks?
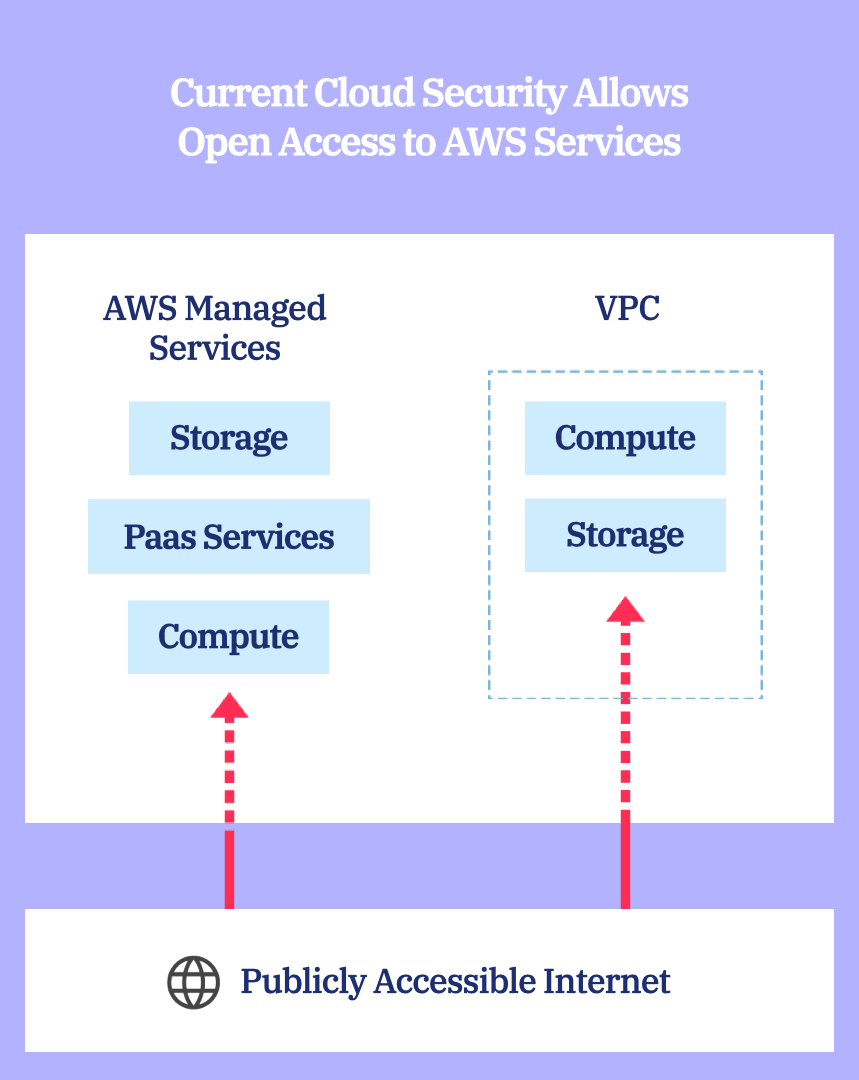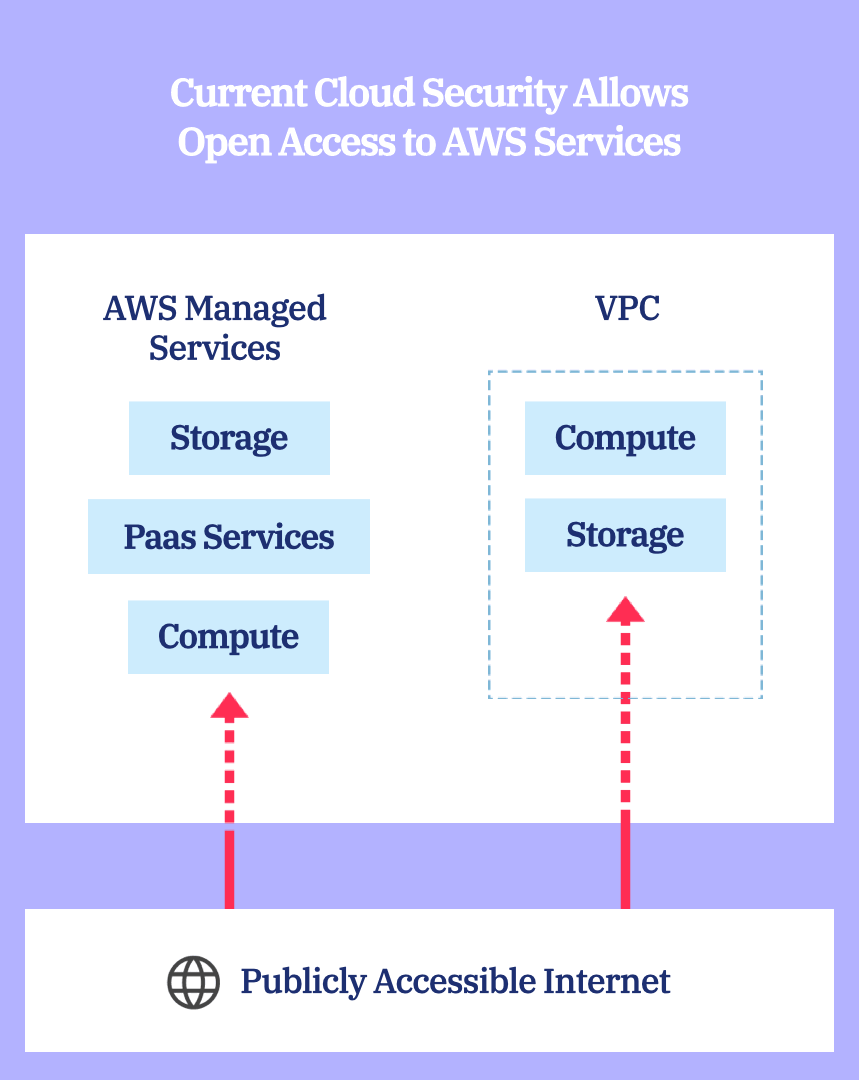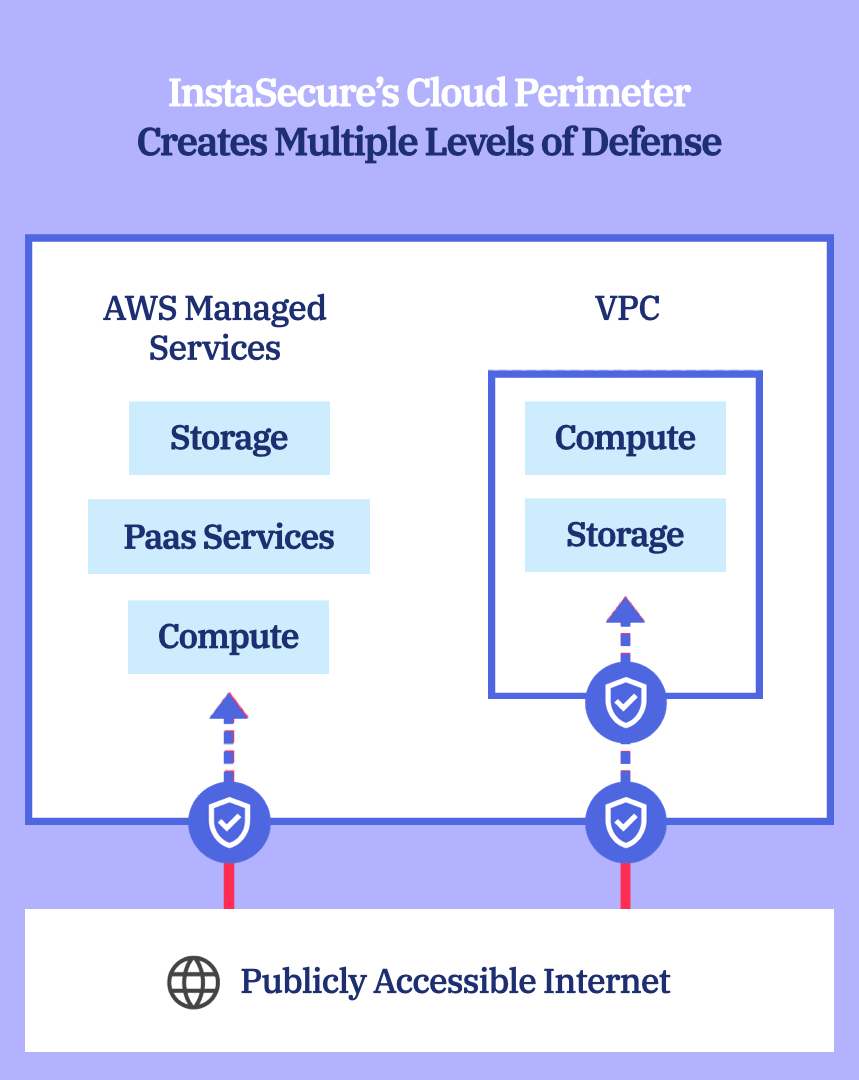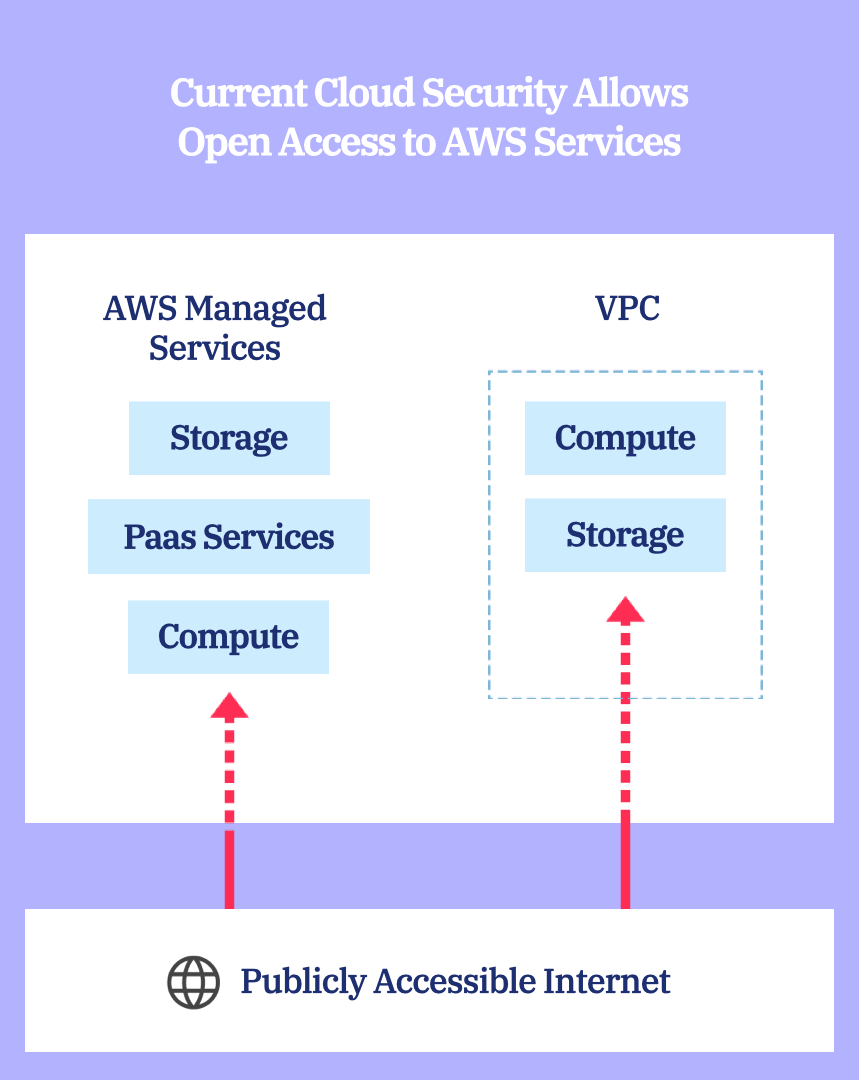
InstaSecure’s Cloud Data Perimeter ensures that only Trusted Identities are accessing Trusted Resources from Expected Networks
Trusted Identities
Cloud principals (service or users) or cloud services acting on your behalf
Cloud Resources owned by your account or Cloud Services acting on your behalf
Trusted Resources
Authorized networks like on-prem data centers, VPN, cloud VPCs or Cloud networks used by Cloud service provider Services
Expected Networks
Our three-dimensional Cloud Data Perimeter Trust Boundary protects against these common threats:
Normally, identities are portable and can be used anywhere. InstaSecure enforces network protections so that stolen credentials can’t be used.
Credential Theft
InstaSecure builds a proactive trust boundary for your cloud infrastructure before attackers can exploit any vulnerabilities.
Zero-Day Attacks
With our Cloud Data Perimeter, uplevel your cloud security defenses and boost your team’s productivity
Go from reactive remediation to proactive prevention
Boost your release velocity by replacing Security Gates with Perimeter Controls
Defend against unknown and Zero-Day vulnerabilities